These instructions assume Microsoft Outlook 2013 is used on a Windows operating system. These are specifically how I add profiles for other Office365 hosted mailboxes without an issue, but these instructions will get you most of the way through adding profiles for on premise or other similar setup you may have.
Another important point to note is that the mailbox you are trying to add must not be hidden from any address list view, you need to be able to see this mailbox in an address book view. If it is hidden, unhide the mailbox, add the profile, then you can hide the profile again afterwards. The user credentials you are specify for mailbox access must also have Full Access permissions to the mailbox you are trying to add.
Browse to Control Panel and click Mail, assuming you already have a profile configured (your own personal email account) it will likely return the Mail Setup screen for the profile you already have configured. Click the Show Profiles… button to return the current list of profiles, ensure that the Prompt for a profile to be used option is selected, click Add…
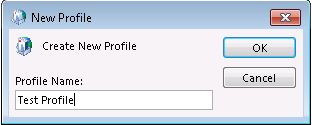
Enter a Profile Name of your choice and click OK >
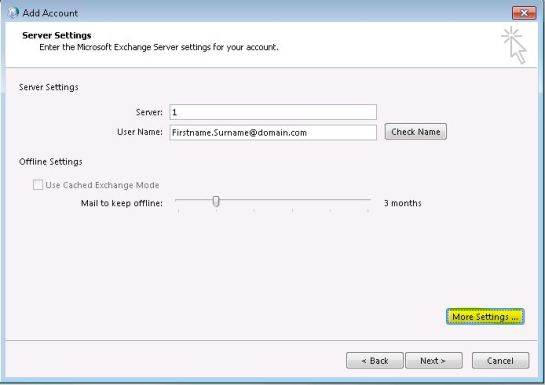
This will launch the Auto Account Setup, I always choose the Manual setup or additional server types option and click Next > Select Microsoft Exchange Server or compatible service and click Next > On the Server Settings screen I always add a dummy entry in the Server section as this isn’t actually used because Outlook Anywhere settings are specified shortly and they use the Autodiscover service to map up correctly. Add the entry of 1 and tab into the User Name section. In here I usually add the primary SMTP address of the mailbox you are wanting to setup in this profile, so for example I would add Firstname.Surname@domain.com but do not click Check Name. I usually disable Offline Settings for secondary profiles particular on shared mailboxes which may be quite large, this is up to you > Now do not click Next, instead click More Settings… >
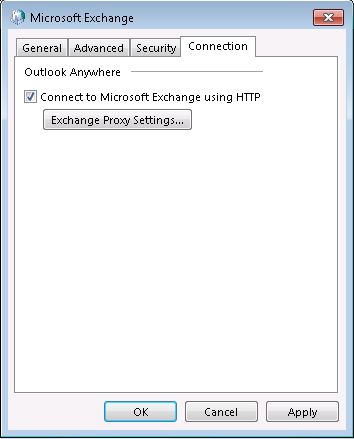
Click into the Connection tab and check the Connect to Microsoft Exchange using HTTP option and click the Exchange Proxy Settings… button >
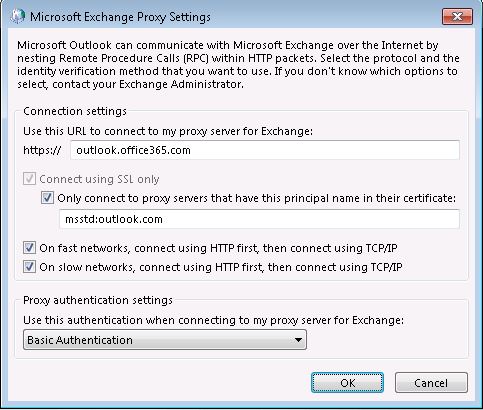
Tick all check boxes and select Basic Authentication in the Proxy authentication settings section. In the top Use this URL to connect to my proxy server for Exchange text box, enter outlook.office365.com and msstd:outlook.com in the Only connect to proxy servers that have this principal name in their certificate text box and click OK >
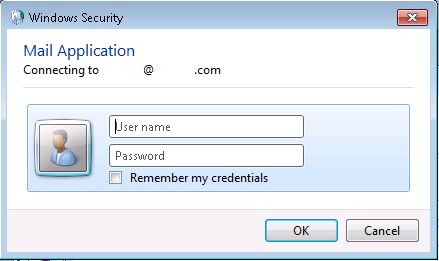
Click OK again on the Microsoft Exchange pop out screen you should have been returned to, this should now return you to the Add Account / Server Settings screen, now click Next > This should now pop up a Windows Security screen prompting for credentials to connect to the mailbox. In here you should provide a fully qualified username e.g. firstname.surname@domain.com and the password for that account, I don’t usually check the Remember my credentials check box but this is up to you, once the credentials are provided once I don’t usually get prompted again for credentials whenever that profile is selected at Outlook startup. Click OK once you have added the credentials >
All being well you should receive the You’re all set ! screen where can now click Finish.